For many organizations, the phrase Security Operations Center, or SOC, conjures a familiar image: a darkened room filled with glowing monitors, analysts staring intently at streams of alerts, ready to stop hackers in their tracks. While this image isn’t entirely wrong, it dramatically understates the role a modern SOC plays in today’s cyber threat landscape.
In reality, a modern Security Operations Center is less about watching blinking lights and more about continuous risk management, rapid decision-making, and organizational resilience. As cyber threats become more sophisticated, automated, and persistent, the SOC has evolved into a nerve center that protects not just infrastructure, but business continuity, reputation, and trust.
So what does a modern SOC actually do, and why do so many organizations struggle to build one that works?
From Alert Factories to Strategic Defense Engines
Early SOCs were largely reactive. Their primary job was to collect logs, trigger alerts, and respond when something went wrong. If an intrusion detection system fired an alarm, analysts investigated. If malware was detected, it was removed. Security was event-driven, manual, and heavily dependent on human vigilance.
Today’s threat environment has rendered that approach obsolete.
Modern attackers don’t rely on noisy exploits. They blend into normal activity, leverage legitimate credentials, and move laterally over weeks or months. A modern SOC must therefore operate with context, intelligence, and foresight, not just alerts.
Instead of asking “What just happened?”, modern SOCs ask:
- What is happening across our environment right now?
- What matters most to the business?
- Which threats pose real risk, and which are noise?
- How do we stop incidents before they become breaches?
This shift, from reactive monitoring to proactive defense,is the defining characteristic of a modern SOC.
Continuous Visibility Across the Entire Attack Surface
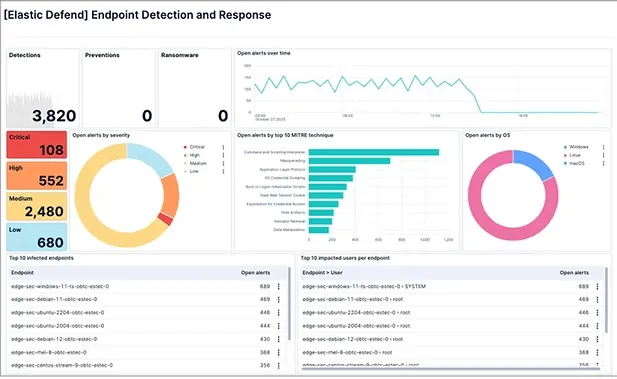
At its core, a SOC exists to maintain continuous visibility. But visibility today extends far beyond traditional networks.
A modern SOC monitors:
- Endpoints such as laptops, servers, and mobile devices
- Cloud workloads and SaaS platforms
- Identity systems and authentication flows
- Network traffic across on-premises and hybrid environments
- Third-party connections and supply chain integrations
This unified visibility is essential because modern attacks rarely stay in one place. An attacker might compromise an endpoint, escalate privileges through identity systems, pivot into cloud resources, and exfiltrate data through encrypted channels—all without triggering a single “critical” alert.
A capable SOC correlates signals across all these domains to identify subtle patterns that would otherwise go unnoticed.
Separating Real Threats from Overwhelming Noise
One of the biggest misconceptions about SOCs is that more alerts equal better security. In reality, alert overload is one of the greatest risks organizations face.
Modern environments generate millions of events per day. Only a fraction represent genuine threats. Without intelligent filtering and prioritization, SOC analysts quickly burn out—or worse, miss the one alert that truly matters.
A modern SOC applies:
- Behavioral analytics to detect anomalies
- Threat intelligence to understand attacker tactics
- Risk-based prioritization aligned to business impact
- Automation to suppress known benign activity
The goal is not to respond to everything, but to respond correctly and quickly to the threats that pose real harm.
Rapid Detection, Investigation, and Response
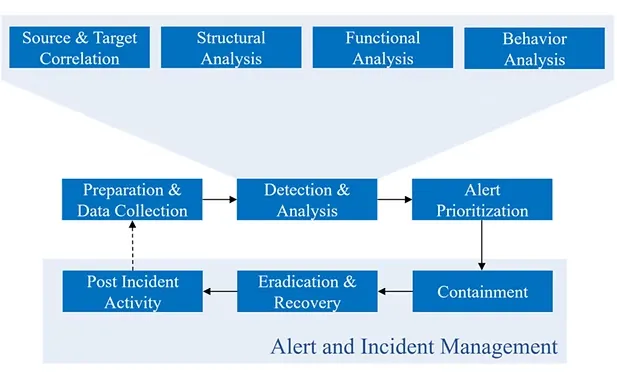
When an incident does occur, time becomes the most critical factor. The difference between a contained incident and a headline-making breach often comes down to minutes, or even seconds.
A modern SOC follows a tightly integrated lifecycle:
- Detection – Identifying suspicious activity early
- Investigation – Understanding scope, intent, and impact
- Containment – Stopping lateral movement and further damage
- Eradication – Removing the attacker’s presence
- Recovery – Restoring systems safely
- Learning – Improving defenses based on what was discovered
Automation and orchestration now play a central role in this process. Routine containment actions, isolating endpoints, disabling accounts, blocking indicators,can happen automatically, freeing analysts to focus on complex decision-making rather than repetitive tasks.
Threat Hunting: Finding What Tools Don’t Detect
While automated detection is critical, modern SOCs don’t rely on tools alone. They actively engage in threat hunting, the practice of proactively searching for hidden or emerging threats that have evaded standard defenses.
Threat hunters use hypotheses based on real-world attacker behavior:
- What would lateral movement look like in our environment?
- How would an attacker abuse our identity systems?
- What does “normal” really mean for our users?
This proactive approach often uncovers dormant threats long before they trigger alerts, dramatically reducing dwell time and potential impact.
Aligning Security Operations with Business Risk
Perhaps the most important evolution of the modern SOC is its alignment with business outcomes.
Security teams are no longer measured solely by how many alerts they close, but by how effectively they:
- Reduce operational risk
- Protect critical assets
- Enable safe digital transformation
- Support compliance and regulatory obligations
A modern SOC speaks the language of the business. It translates technical findings into clear risk narratives that executives can understand and act upon. This shift transforms the SOC from a cost center into a strategic asset.
Why Building a Modern SOC Is So Hard
Despite its importance, many organizations struggle to operate an effective SOC. Skills shortages, tool sprawl, budget constraints, and 24/7 coverage requirements make in-house SOCs difficult to sustain.
Even well-resourced teams face challenges such as:
- Alert fatigue and analyst burnout
- Inconsistent visibility across environments
- Slow incident response times
- Difficulty keeping up with evolving threats
This is where specialized cybersecurity partners become essential.
How Armour Cybersecurity Helps Organizations Modernize Their SOC
Armour Cybersecurity helps organizations overcome these challenges by delivering managed, intelligence-driven security operations designed for today’s threat landscape.
Armour’s approach combines:
- 24/7 monitoring by experienced security professionals
- Advanced detection and response across endpoints, cloud, and identity
- Threat intelligence informed by real-world adversary behavior
- Automated response to reduce risk and response time
- Clear, actionable reporting aligned to business priorities
Rather than forcing organizations to build and maintain complex SOC infrastructure on their own, Armour provides the expertise, technology, and operational maturity required to stay ahead of modern threats.
The Future of the SOC Is Already Here
The modern Security Operations Center is no longer just a room, a dashboard, or a team reacting to alerts. It is a living, adaptive capability that continuously protects the business from evolving cyber risk.
Organizations that embrace this modern SOC model gain more than stronger security—they gain confidence to innovate, scale, and operate in a digital-first world.
Those that don’t risk being outpaced by attackers who are faster, smarter, and increasingly automated.
Ready to Strengthen Your Security Operations?
Armour Cybersecurity helps organizations build and operate modern SOC capabilities without the complexity and cost of doing it alone.
Talk to Armour Cybersecurity today to see how managed detection and response, threat hunting, and 24/7 security operations can protect your business, before attackers make their move.