Cybersecurity in 2025 reached a turning point. What was once viewed as a technical issue became a core business, governance, and operational risk. Across industries, organizations faced an increasingly complex threat landscape defined by ransomware, phishing, identity abuse, and exploited vulnerabilities, all confirmed by global cybersecurity research and breach investigations.
This article provides a summary of cybersecurity developments in 2025, followed by data-driven predictions for 2026.
The State of Cybersecurity in 2025
Cybercrime Continued to Increase Worldwide
Throughout 2025, global cybersecurity reports confirmed a sustained rise in:
- The number of cyberattacks per organization
- The financial impact of data breaches
- The time required to detect and contain incidents
IBM’s Cost of a Data Breach Report 2025 puts the global average breach cost at $4.44M. Indirect costs such as downtime, legal exposure, and lost trust, often exceed the direct technical recovery work.
Industries most frequently targeted included:
- Healthcare
- Government and public sector
- Education
- Financial services
- Manufacturing and critical infrastructure
These sectors remain attractive targets due to high operational dependency on IT systems and limited tolerance for disruption.
Ransomware in 2025: Fewer Headlines, Greater Impact
Ransomware did not disappear in 2025, it matured.
Attackers increasingly focused on:
- Data theft before encryption
- Targeted system disruption rather than full network shutdowns
- Extortion through leaked data rather than public spectacle
This shift made ransomware attacks harder to detect early and more damaging over time. Even organizations that avoided paying ransoms often faced prolonged exposure due to stolen data, regulatory reporting obligations, and legal scrutiny.
Phishing and Social Engineering Remained the Leading Attack Vector
Verified breach analyses consistently identified phishing and stolen credentials as the most common initial access methods.
In 2025, phishing attacks became:
- Shorter and more believable
- Context-aware, referencing real business processes
- Focused on finance teams, executives, and IT administrators
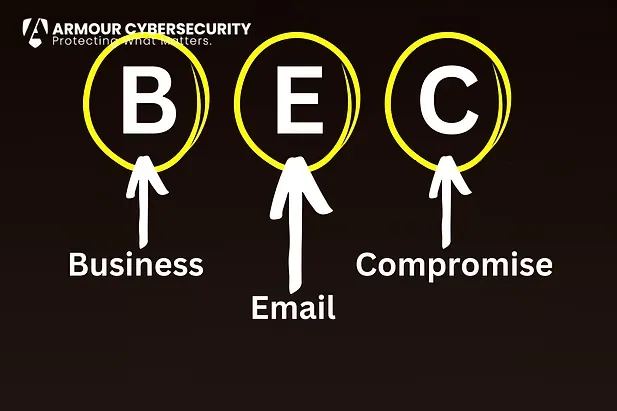
Business email compromise (BEC) attacks, including invoice fraud and payroll diversion continued to cause significant financial losses without requiring malware, reinforcing that human trust remains a primary attack surface.
Artificial Intelligence in Cybersecurity: Evolution, Not Explosion
Despite widespread speculation, 2025 did not see AI fundamentally replace human attackers or defenders.
Instead, AI was used to:
- Improve phishing quality and language
- Speed up reconnaissance and data analysis
- Assist with automation on both offense and defense
Security teams also increasingly relied on AI-driven tools for behavioral detection, alert prioritization, and anomaly analysis. AI functioned as a force multiplier, not an independent actor.
Exploited Vulnerabilities and Patch Delays Remained a Major Risk
Throughout 2025, organizations continued to struggle with:
- Timely patching of known vulnerabilities
- Securing externally facing systems
- Managing legacy and hybrid environments
Confirmed incidents repeatedly showed attackers exploiting vulnerabilities that were already documented and patched, but not yet addressed by affected organizations. This reinforced a long-standing cybersecurity reality: patch management failures remain one of the most common causes of breaches.
Human Error Still Played a Central Role in Breaches
Investigations in 2025 consistently highlighted non-technical causes such as:
- Misconfigured cloud services
- Overprivileged user accounts
- Weak identity governance
- Missing or improperly enforced multi-factor authentication
While security tools improved, process maturity and user behavior continued to lag behind technological capability.
Cybersecurity Predictions for 2026
Based on verified trends and industry consensus, the following developments are likely to define cybersecurity in 2026.
1. Identity Security Will Become the Primary Control Layer
Attackers increasingly bypass perimeter defenses by targeting:
- Credentials
- Session tokens
- OAuth permissions
- MFA fatigue techniques
In 2026, identity protection – not network security – will be the primary focus of breach prevention strategies.
2. Regulatory and Legal Pressure Will Increase
Governments and regulators are moving toward:
- Faster breach disclosure timelines
- Greater enforcement of cybersecurity standards
- Increased accountability for executive leadership
Cybersecurity will continue shifting from a technical responsibility to a board-level governance issue.
3. Small and Mid-Sized Businesses Will Face Higher Risk
As larger organizations improve defenses, attackers are expected to:
- Target SMBs with weaker security controls
- Exploit trusted third-party relationships
- Leverage managed service providers as access points
Security maturity, not organization size, will define exposure in 2026.
4. AI Will Increase Speed and Scale on Both Sides
AI adoption will likely:
- Reduce attacker effort and cost
- Improve defensive detection and response speed
- Increase reliance on automation to manage alert volume
Organizations that fail to integrate AI strategically may struggle to keep pace.
5. Cyber Resilience Will Matter More Than Prevention Alone
In 2026, organizations will increasingly prioritize:
- Incident response readiness
- Business continuity planning
- Decision-making during prolonged outages
The question will shift from “Can we prevent an attack?” to “How quickly can we recover?”
Conclusion: The Lasting Lesson of 2025
Cybersecurity in 2025 did not introduce entirely new threats, it exposed long-standing weaknesses.
The organizations that weathered incidents most effectively were not those with the most tools, but those with:
- Clear response plans
- Strong identity controls
- Executive involvement
- Realistic expectations
As 2026 approaches, one fact is undeniable:Cybersecurity is no longer optional, invisible, or delegable. It is a core operational reality.
Cybersecurity 2026: Reader Questions & Expert Answers
Q1: What will be the biggest cybersecurity threat in 2026?
A: Identity-based attacks are expected to be the most significant cybersecurity threat in 2026. Attackers are increasingly bypassing traditional defenses by stealing credentials, abusing OAuth permissions, and exploiting session tokens. As organizations rely more on cloud services and remote access, identity has become the primary attack surface.
Q2: How should organizations prepare for cybersecurity risks in 2026?
A: Preparation for 2026 should focus on identity security, incident response readiness, and resilience planning. This includes enforcing multi-factor authentication, reducing user privileges, improving patch management, and regularly testing incident response and business continuity plans.
Q3: Will ransomware still be a major threat in 2026?
A: Yes. Ransomware is expected to continue evolving rather than disappearing. In 2026, attacks will likely focus more on data theft, targeted disruption, and extortion rather than full network encryption. Organizations should prioritize data protection, backup validation, and rapid detection over ransom payment strategies.
Q4: How will artificial intelligence impact cyberattacks in 2026?
A: Artificial intelligence will primarily increase the speed and efficiency of attacks rather than create entirely new types of threats. Attackers may use AI to improve phishing campaigns and automate reconnaissance, while defenders will rely on AI to detect anomalies, prioritize alerts, and reduce response times.
Q5: Are small and mid-sized businesses more at risk in 2026?
A: Small and mid-sized businesses are expected to face increased targeting in 2026 due to limited security resources and their role in larger supply chains. Attackers often view SMBs as easier entry points into larger organizations, making baseline security controls essential regardless of company size.
Q6: What cybersecurity controls will matter most going into 2026?
A: Identity protection, multi-factor authentication, endpoint visibility, patch management, and secure backups will remain the most critical controls. Organizations that focus on fewer, well-implemented controls tend to perform better than those relying on many underused tools.
Q7: Will compliance and regulations increase cybersecurity pressure in 2026?
A: Yes. Regulatory requirements around breach disclosure, data protection, and accountability are expected to continue tightening. Organizations should treat compliance as a baseline rather than a security strategy and align technical controls with governance and risk management expectations.
Q8: How can organizations reduce the impact of a cyber incident in 2026?
A: Reducing impact requires preparation, not just prevention. Regular incident response exercises, clear escalation paths, offline backups, and decision-making authority defined in advance all help organizations respond faster and limit damage during a real incident.
Q9: What role will cybersecurity leadership play in 2026?
A: Cybersecurity leadership will increasingly shift toward strategic risk management. Leaders will be expected to communicate cyber risk in business terms, support investment decisions, and coordinate across legal, operations, and executive teams during incidents.
Q10: Is it realistic to aim for full cyberattack prevention in 2026?
A: No organization can realistically prevent every cyberattack. In 2026, success will be defined by how quickly threats are detected, how effectively incidents are contained, and how well business operations can continue during disruption.
Q11: What is the most important mindset shift organizations need for 2026?
A: The most important shift is moving from a prevention-only mindset to a resilience-focused approach. Organizations must assume breaches are possible and plan accordingly, emphasizing recovery, communication, and continuity.
Q12: How should boards and executives engage with cybersecurity planning for 2026?
A: Boards should ask practical questions about recovery time, incident ownership, and operational impact rather than focusing solely on technical controls. Cybersecurity planning should be integrated into enterprise risk management and business continuity discussions.
Cybersecurity Is a Leadership Decision – Not Just a Technical One
In 2026, cybersecurity will continue moving out of the IT department and into the boardroom. Executives and boards are increasingly expected to understand not just if an attack happens, but how the organization responds.
If your leadership team cannot confidently answer questions about recovery time, decision ownership, and operational impact, it may be time to reassess your cybersecurity strategy.