Cyber threats are increasingly stealthy, sophisticated, and capable of evading traditional security defenses. Standard tools like firewalls and antivirus software alone aren’t enough to protect sensitive data. That’s where cyber threat hunting comes in—a proactive, intelligence-driven approach to identifying and neutralizing hidden threats before they cause harm.
This article explores what cyber threat hunting is, why it matters, how to implement a practical model, and how Armour Cybersecurity can help organizations do it effectively.
What Is Cyber Threat Hunting?
Cyber threat hunting is the process of actively seeking out cyber threats that have evaded detection. Instead of waiting for automated alerts, security analysts formulate hypotheses, analyze data, and uncover signs of compromise manually or semi-automatically.
This proactive approach assumes that attackers may already be inside the network and focuses on finding them before they execute damaging actions.
Why Threat Hunting Matters
Many cyberattacks, including ransomware, data breaches, and insider threats, go undetected for weeks or months. During that time, attackers can steal data, compromise systems, or install backdoors for future attacks.
Threat hunting delivers:
- Faster detection and containment of sophisticated threats
- Shorter dwell times, reducing attacker impact
- Improved response coordination
- Insights into attacker behavior to enhance defenses
- Stronger risk posture across the organization
The Cyber Threat Hunting Lifecycle
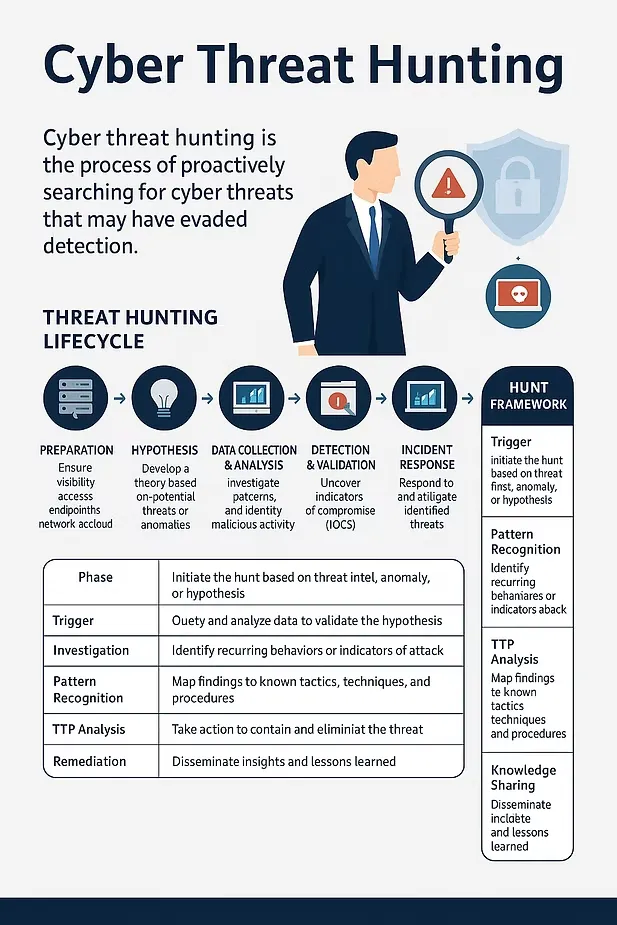
1. Preparation
Organizations need the right visibility across endpoints, networks, cloud, and identity systems. This includes collecting logs, integrating threat intelligence, and staffing skilled analysts.
2. Hypothesis Generation
A hunt begins with a theory—for example: “An attacker may have bypassed MFA using stolen credentials.” These hypotheses are based on threat intelligence, prior incidents, or observed anomalies.
3. Data Collection & Analysis
Analysts investigate patterns in endpoint logs, DNS queries, authentication logs, and user behavior. Normalizing data is key to spotting relationships that may indicate malicious behavior.
4. Detection & Validation
The team searches for indicators of compromise (IOCs), behavioral anomalies, and adversary techniques—often using frameworks like MITRE ATT&CK to guide detection.
5. Incident Response
If threats are confirmed, rapid response is critical—isolating hosts, disabling accounts, and eradicating malicious files.
6. Feedback & Improvement
Hunt results inform SIEM rules, detection signatures, and future hunts, contributing to a continuously improving defense.
A Practical Model: The HUNT Framework
The HUNT Framework offers a structured approach to cyber threat hunting:
| Phase | Description |
| Trigger | Start a hunt based on threat intel, anomaly, or hypothesis |
| Investigation | Query and correlate data to find evidence of the threat |
| Pattern Recognition | Spot repeating indicators or attack behaviors |
| TTP Analysis | Map attacker tactics to known frameworks (e.g., MITRE ATT&CK) |
| Remediation | Take corrective actions to contain and remove the threat |
| Knowledge Sharing | Update internal detection tools and inform security teams |
This framework helps teams build repeatable, strategic threat hunting practices.
How Armour Cybersecurity Can Help
Armour Cybersecurity offers expert-driven, intelligence-led threat hunting services tailored to your industry, infrastructure, and risk profile.
Here’s how Armour supports your cyber threat hunting needs:
End-to-End Threat Hunting Programs
Armour Cybersecurity helps design, deploy, and manage threat hunting programs—whether you need a one-time investigation or an ongoing service.
Security Maturity Assessments
We assess your current logging, detection, and incident response capabilities to identify gaps and areas of improvement.
Threat Intelligence Integration
Armour Cybersecurity integrates real-time threat intel feeds with your data environment to fuel more accurate and targeted hunts.
Experienced Cyber Analysts
Our team includes seasoned threat hunters, forensics experts, and incident responders with experience across industries and threat types.
Customized Hunting Playbooks
Armour Cybersecurity develops organization-specific hunting playbooks aligned with your business goals, regulatory needs, and threat landscape.
Continuous Improvement
Post-hunt reports from Armour Cybersecurity provide actionable insights, detection rule updates, and long-term defense enhancements.
Whether you’re starting from scratch or scaling an existing cybersecurity program, Armour Cybersecurity enables you to move from reactive defense to proactive threat hunting—before threats cause damage.
Final Thoughts
Cyber threat hunting empowers organizations to stay one step ahead of attackers by proactively identifying and responding to hidden threats. By implementing structured models like the HUNT Framework, businesses can significantly reduce dwell time and enhance their overall security posture.
Partnering with a trusted cybersecurity firm like Armour Cybersecurity ensures that your team has the tools, expertise, and strategy to hunt threats effectively and continuously improve your defenses.
Want to learn more about how Armour Cybersecurity can help you build a world-class threat hunting program?
Visit our website or contact us for a free consultation.
Frequently Asked Questions (FAQs)
Q: How does threat hunting differ from automated threat detection?
A: Threat hunting is a proactive, hypothesis-driven activity led by humans, whereas automated detection relies on predefined rules and alerts to identify known threats.
Q: Can threat hunting uncover non-malicious security issues?
A: Yes. Threat hunts often reveal misconfigurations, policy violations, or risky behaviors that may not be malicious but still increase exposure.
Q: Can threat hunting help detect insider threats?
A: Yes. By analyzing behavior rather than relying solely on alerts, threat hunting can uncover suspicious activity from trusted or privileged users.



