Businesses must prioritize a proactive and comprehensive approach to cybersecurity. One of the most crucial concepts in this domain is security posture, a holistic measure of an organization’s overall cybersecurity health. From cloud environments to data protection, understanding and managing security posture has become vital for digital resilience.
In this article, we’ll break down what security posture means, explore the tools and strategies like Cloud Security Posture Management (CSPM) and Data Security Posture Management (DSPM), and highlight their benefits for organizations of all sizes.
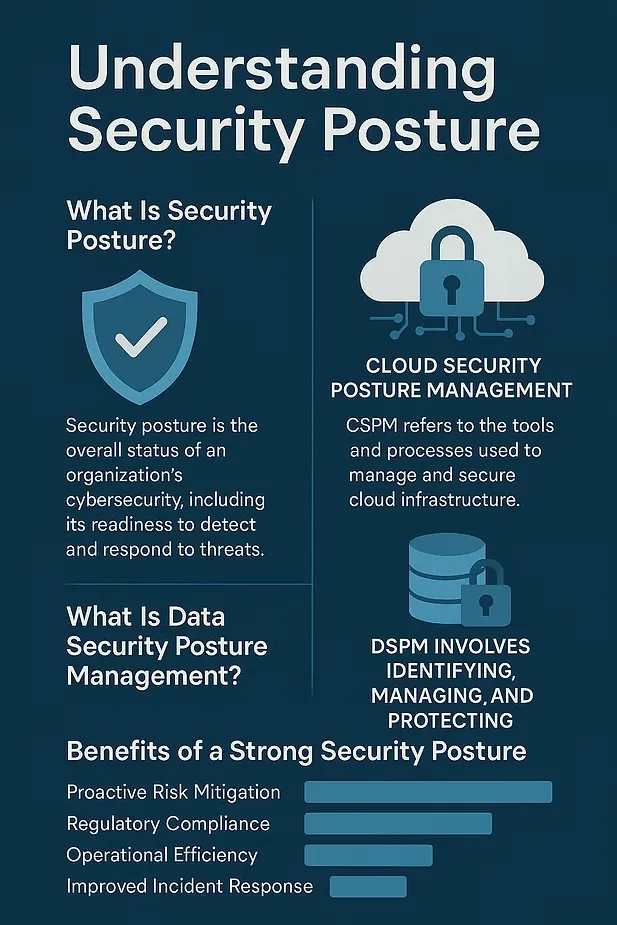
What Is Security Posture?
Security posture refers to the overall status and strength of an organization’s cybersecurity efforts. It encompasses all the strategies, processes, policies, and tools in place to protect digital assets, detect and respond to threats, and recover from cyber incidents.
Key elements of security posture include:
- Preventative controls (e.g., firewalls, anti-malware, access controls)
- Detective controls (e.g., intrusion detection systems, monitoring)
- Responsive strategies (e.g., incident response plans, recovery protocols)
- Compliance alignment (e.g., with GDPR, HIPAA, or ISO standards)
Essentially, your security posture answers the question: How well is your organization prepared to defend against and respond to cyber threats?
Why Is Security Posture Important?
A weak or undefined security posture exposes organizations to:
- Data breaches
- Ransomware attacks
- Regulatory penalties
- Brand reputation damage
- Financial loss
With digital transformation and cloud adoption on the rise, the traditional security perimeter has dissolved. This has made real-time visibility, configuration management, and data control essential components of a robust cybersecurity framework.
What Is Cloud Security Posture Management (CSPM)?
Cloud Security Posture Management (CSPM) is a class of tools and practices designed to automatically identify and remediate risks in cloud environments. As more organizations migrate workloads to the cloud, managing misconfigurations and compliance across complex infrastructures becomes challenging.
CSPM tools offer continuous monitoring and assessment of cloud services, such as:
- Amazon Web Services (AWS)
- Microsoft Azure
- Google Cloud Platform (GCP)
Core Features of CSPM:
- Misconfiguration detection: Identifies unsafe settings like open storage buckets or exposed ports.
- Compliance monitoring: Ensures alignment with standards like CIS Benchmarks, SOC 2, and NIST.
- Automated remediation: Applies fixes or alerts teams to potential vulnerabilities.
- Visibility and inventory: Tracks assets, identities, and network flows.
By implementing CSPM, organizations gain a real-time understanding of their cloud environment’s security posture and can proactively eliminate potential threats before they are exploited.
What Is Data Security Posture Management (DSPM)?
Data Security Posture Management (DSPM) focuses specifically on identifying, managing, and protecting sensitive data across an organization’s digital ecosystem. Unlike CSPM, which targets infrastructure, DSPM zeroes in on the data itself.
In today’s hybrid environments, where data lives across on-premises systems, cloud storage, SaaS platforms, and endpoints, knowing where your critical data resides and how it’s accessed is paramount.
Key Capabilities of DSPM:
- Data discovery and classification: Locates sensitive data like PII, PHI, and intellectual property.
- Risk assessment: Evaluates who has access to the data and how it’s being used.
- Access control: Implements least privilege policies and monitors for anomalous behavior.
- Encryption and tokenization: Protects data in transit and at rest.
- Audit and compliance reporting: Demonstrates data security for regulatory frameworks such as GDPR or CCPA.
DSPM tools give security teams the visibility and control needed to reduce the attack surface and prevent unauthorized access or data leakage.
Benefits of a Strong Security Posture
Whether you’re securing infrastructure with CSPM or safeguarding sensitive information via DSPM, investing in your organization’s security posture yields several critical advantages:
1. Proactive Risk Mitigation
Rather than reacting to threats after they occur, a strong posture allows you to identify vulnerabilities early and apply corrective measures, drastically reducing the window of opportunity for attackers.
2. Regulatory Compliance
Many industries are governed by strict data protection and cybersecurity regulations. A well-defined security posture ensures ongoing compliance with standards like PCI DSS, HIPAA, and ISO 27001.
3. Operational Efficiency
Security posture tools often automate the discovery and remediation of risks, reducing manual work and freeing up security teams to focus on strategic initiatives.
4. Enhanced Visibility
You can’t protect what you can’t see. CSPM and DSPM solutions provide centralized dashboards and reports that offer clarity into your entire digital ecosystem.
5. Improved Incident Response
When breaches do occur, having a comprehensive understanding of your security posture enables faster detection, containment, and recovery—minimizing damage and downtime.
6. Customer Trust
Consumers and partners increasingly value privacy and data protection. A strong security posture demonstrates your commitment to cybersecurity, strengthening your brand and customer relationships.
Best Practices to Improve Security Posture
To build and maintain a solid security posture, organizations should:
- Conduct regular risk assessments across cloud and on-prem environments.
- Implement continuous monitoring to detect real-time threats.
- Adopt zero trust architecture to minimize lateral movement in networks.
- Train employees on cybersecurity best practices.
- Integrate CSPM and DSPM tools into existing workflows.
- Establish and rehearse incident response plans.
Final Thoughts
Security posture is more than a buzzword, it’s a critical metric of how prepared your organization is to handle today’s evolving threat landscape. By investing in Cloud Security Posture Management (CSPM) and Data Security Posture Management (DSPM), companies can gain visibility, reduce risk, and enhance their resilience against cyber attacks.
In today’s digital-first world, your security posture isn’t just an IT concern, it’s a business imperative. Taking a proactive, posture-centric approach to cybersecurity is no longer optional; it’s essential for long-term success.
Frequently Asked Questions (FAQs)
Q: How often should an organization formally reassess its security posture?
A: Security posture should be reassessed regularly and after major changes such as new technologies, mergers, cloud migrations, or significant threat activity.
Q: How does employee behavior impact overall security posture?
A: Human behavior plays a major role. Even strong technical controls can be undermined by poor security awareness or inconsistent adherence to policies.
Q: What role do third-party vendors play in security posture risk?
A: Vendors can introduce significant risk if their controls are weaker, making third-party risk management a critical part of overall posture.



